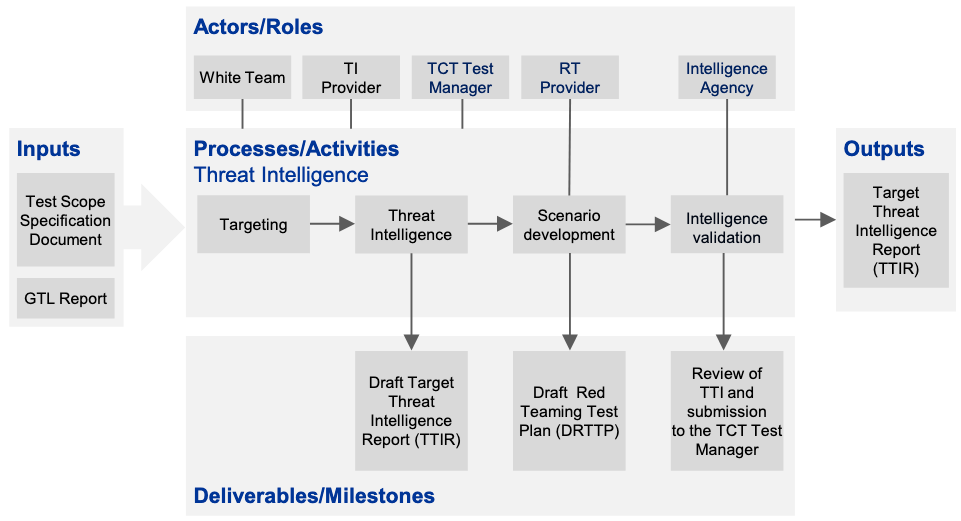
Testing phase: threat intelligence and scenarios
Overview
Once the scope has been agreed, the TI/RT providers have been contracted, and all parties have been informed of their roles and responsibilities, the testing phase should commence, with threat intelligence a key component. Threat intelligence- based scenarios mimicking real-life cyber adversaries are essential to the success of testing activities. There are two complementary tools to develop these threat intelligence-based scenarios: the GTL Report and the TTI Report. The duration of the targeted threat intelligence process in this phase is approximately five weeks.
The GTL Report should reflect the most significant threats faced by the financial sector, whether at a national or European level. The GTL Report can be used to develop the TTI Report, which gives a more detailed view of the specific entity’s current defences and attack surface and helps produce actionable and realistic attack scenarios. Such attack scenarios look to emulate the TTPs of real-life threat actors within a threat landscape and will be used to deliver a realistic simulation. These scenarios will be integrated into the RT provider’s Red Team Test Plan and help the RT provider to deliver a practical assessment of the entity’s defensive security controls, and its detection and response capabilities.
Generic threat landscape
Given the critical role of threat intelligence to a TIBER-EU test, entities must procure a TTI Report, which sets out the specific threat scenarios they may be faced with. The scenarios will allow the RT provider to conduct a realistic and meaningful test. However, the TIBER-EU framework recommends that national jurisdictions first produce a national GTL Report for the financial sector to complement the more specific TTI Report.
The GTL Report should elaborate on the specific threat landscape of the country, taking into consideration the geopolitical and criminal threats unique to the jurisdiction. The report should consider key financial market participants and their CFs, including (wholesale and retail) banks, broker-dealers, financial market infrastructures, financial market utilities, and other critical third parties, the different threat actors (including their TTPs) targeting these entities, and the common vulnerabilities. The GTL Report is used to define the specific threat actors targeting the different types of entities, complements the production of the TTI Report and provides the basis for later scenario development. If produced at an early stage of the process, the GTL Report should also be used during the preparation phase to guide and inform the initial scoping discussions with the entity.
The GTL Report will allow TI providers to:
- help translate the information contained in the GTL Report into specific strategic, operational and tactical threat intelligence that is relevant to the entity;
- focus their efforts on more detailed reconnaissance to provide the RT provider with more bespoke and specific information on the entity, which will in turn allow meaningful attack scenarios to be developed and a more effective test to be performed.
The GTL Report aims to provide TI providers with a solid base of information and analysis, which can then be used to produce more entity-specific TTI Reports. Although a GTL Report is not mandatory, it can be more cost-effective for the financial sector in each jurisdiction to produce one, with each TI provider and entity using it as a common tool when developing the more specific TTI Reports.
Production and ownership of the GTL Report
The GTL Report may be instigated and produced by the authority, the market (e.g. industry bodies, a consortium of entities or any other financial sector body), or both in partnership. The report may also be produced by external providers. In any case, it is recommended that the report be shared more widely with the financial sector. To provide a broad and realistic overview of the threat to the national (and possibly European) financial sector, the GTL Report should be developed using appropriate financial sector threat intelligence expertise. Appropriate threat intelligence expertise can be sourced from entities, national authorities, commercial TI providers, information sharing and analysis centres (ISACs), market associations and government agencies.
As the threat landscape is constantly evolving, the GTL Report should be updated on an ongoing basis as new threat actors, TTPs and vulnerabilities enter the landscape. Updates should be carried out at least annually.
The TI provider should connect the GTL Report to the TTI Report (explained in more detail below) to develop specific threat scenarios for the targeted entity. The RT provider should be consulted to ensure the scenarios are actionable.
Governmental intelligence
If possible, at national level the GTL Report should be offered to the national intelligence agency – and any other relevant governmental agencies1 – for feedback and further enrichment, and ideally for validation.
In some cases, the GTL Report may also be shared with the European Union Agency for Network and Information Security (ENISA) for feedback and enhancement. If it is not feasible for national intelligence agencies or any other relevant governmental agencies to provide feedback on the report, authorities may seek to consult with a financial sector group with expertise in threat intelligence.
Targeted threat intelligence process
The targeted threat intelligence process results in the production of a TTI Report, which is a bespoke, focused threat intelligence report for the entity being tested. Its aim is to use specific targeted threat intelligence and reconnaissance related to the entity, taking into consideration the real-life actors within the threat landscape, to help develop attack scenarios. Responsibility for the development and production of the TTI Report lies with the TI provider. The RT provider2 becomes involved towards the end of the phase when it absorbs the contents of the TTI Report and integrates the attack scenarios into a Red Team Test Plan.
The TIBER-EU process is designed to create realistic threat scenarios describing attacks against an entity. These scenarios can be used by a simulated attack team to guide its red team test. The scenarios are based on available evidence of real-world threat actors, combined with OSINT data on the entity as well as some knowledge of the CFs that form the scope and target of the red team test.
While this approach is highly valuable, real-world threat actors may have months to prepare an attack. In addition, while TI providers are constrained by limitations on the time and resources available, and by moral, ethical and legal boundaries, real- word threat actors are free of such constraints. This difference can cause difficulties when attempting to create realistic scenarios, as knowledge about the internal network is often the hardest to gain using morally, ethically or legally justifiable techniques.
Similar constraints apply to CFs, which are, by their nature, internal to the entity and so typically do not have a large footprint in the public domain. They also apply to the systems that underpin CFs, whether these are bespoke internal systems or external systems that span multiple organisations with a common connecting infrastructure.
Therefore, to make intelligence gathering as efficient as possible given the time and resource constraints, and to ensure the intelligence is relevant to the scope and the entity’s business, the TI provider should seek from the entity and be provided with:
- a business and technical overview of each CF-supporting system in scope;
- the current threat assessment and/or threat register;
- examples of recent attacks.
The entity should provide the above information to the TI provider in the “Input for the Targeted Threat Intelligence” template.
In cases where the entity has an internal threat intelligence capability or function, the TI provider should liaise with it and gather relevant information that will help inform the TTI Report.
Finally, in cases where the national jurisdiction has produced a GTL Report, the TI provider should use this as a basis for producing the TTI Report, focusing on how to adapt the threat landscape of the country, the different threat actors and the common vulnerabilities to the specificities of the entity.
Elements of the targeted threat intelligence process
During the targeted threat intelligence process, the TI provider collects, analyses and disseminates CF-focused intelligence relating to two key areas of interest:
- target: intelligence or information on potential attack surfaces across the entity;
- threat: intelligence or information on relevant threat actors and probable threat scenarios.
Information gathered from targeting and threat intelligence, in part provided through the Input for the Targeted Threat Intelligence template, should be used to facilitate scenario development (see Section 8.10 below).
Target identification
To identify targets, the TI provider should carry out a broad exercise of the kind typically undertaken by threat actors as they prepare for their attack from outside the network. The objective is to form a detailed preliminary picture of the entity and its weak points from the attacker’s perspective. This will enable the threat intelligence to be put into context and will contribute to the development of the threat scenarios in the TTI Report. Part of this information should be provided by the entity using the Input for the Targeted Threat Intelligence template.
The output of this activity is the identification, on a CF-focused, system-by-system basis, of the attack surfaces of people, processes and technologies relating to the entity, and its global digital footprint. This includes information that is intentionally published by the entity and internal information that has been unintentionally leaked. Such information could be customer data, confidential material or other information that could prove to be a useful resource for an attacker.
Targeting represents a valuable input and is a core element of the TTI Report, where it is used to tailor the threat profile and scenarios. By revealing some of the entity’s attack surfaces and identifying initial targets, it also serves as a valuable input into the RT provider’s deeper and more focused targeting activities.
Threat identification
With regard to threats, the TI provider collects, analyses and disseminates intelligence about relevant threat actors and probable threat scenarios. The objective is to present a credible picture of the cyber threat landscape, based on evidence- backed threat intelligence which is specifically tailored to the entity’s business environment. In cases where a GTL Report has been produced, the TI provider can use it to further complement the identification of threats.
The output resulting from the threat identification process is a summary of the key threats, detailed profiles of the threats with the highest scores, and potential scenarios in which a high-scoring threat actor might target the entity.
As mentioned above, this part of the report builds on intelligence acquired during the target identification process. For example, any relevant assets identified (such as an exposed insecure server) will be integrated into scenarios so the RT provider can exploit them. While the ultimate goal is to find intelligence directly relating to the CFs in scope, these CFs are by their nature buried within the entity’s organisation. In addition, while CF-specific intelligence evidence may not always be discoverable, the TI provider may find evidence of a more general threat that applies to one or more CFs.
While the threat scenarios in this report are fictional, they are based on real-life examples of cyber attacks including the motivations of the attackers, their objectives, and the methods they employ to meet them. By focusing on what is probable rather than theoretically possible, the threat identification part of the TTI Report supports the RT provider in justifying the approach it plans to take.
Targeted Threat Intelligence Report
Equipped with the output from target identification and threat identification, which make up the TTI Report, the TI and RT providers will have a firm evidential basis for the proposed red team test, which include the attack scenarios. Three outputs are particularly relevant in this respect:
- tailored scenarios, which will support the formulation of a realistic and effective Red Team Test Plan;
- threat actor goals and motivations, which will help steer the RT provider in its attempt to capture the flags agreed upon in the Scoping Phase;
- validated evidence which will underpin the business case for post-test remediation and improvement.
The TI provider should complete the TTI Report and then share it with the entity, the TTM and the RT provider. A thorough review should be undertaken, with any factual errors corrected and any issues discussed.
In addition, based on the TTI Report, the WT and TTM may opt to update or modify the flags.
Scenario development
Scenario development represents the key transition point between the TI and RT providers. This activity takes place either just before or in parallel with the national intelligence agency evaluation (where applicable) of the TTI Report (see Section 8.11 below).
Using the scenarios contained in the TTI Report, and in line with the TIBER-EU Test Scope Specification, the RT provider should develop and integrate the attack scenarios into a draft Red Team Test Plan. At this stage, a workshop may be held, involving the entity , TTM and TI/RT providers, during which the TI provider goes through the scenarios and the RT provider goes through the draft Red Team Test Plan (see Section 8.11 below).
Intelligence feedback
Where possible, jurisdictions may seek feedback on the TTI Report from their respective national intelligence agencies or other governmental agencies, such as the national cyber security centre, national high-tech crime unit, military intelligence agency, etc. During the intelligence feedback process, the relevant agencies should review the draft versions of the TTI Report and liaise directly with the TTM with any comments and enhancements.
After the intelligence feedback process, a threat intelligence/scenario workshop must be held involving all relevant stakeholders, namely the entity’s WT, the TTM (and possibly the supervisor and/or overseer) and the TI/RT providers. The workshop activities are as follows:
- the TI provider presents an overview of the TTI Report and summarises the proposed changes to the reports following feedback from the national intelligence agency and/or other agencies;
- the TTM provides feedback comments on the TTI Report;
- the RT provider presents the draft Red Team Test Plan, including CF scenario mapping, flags, possible anticipated leg-ups3 , risk mitigation, escalation procedures, test start/stop dates and a draft Red Team Test Report delivery date.
Following the workshop, the TI provider should revise and produce a final version of the TTI Report for delivery to the entity.
In addition, the RT provider should revise the draft Red Team Test Plan in the light of the workshop findings and the risks identified.
Key considerations for the TI provider
For the TIBER-EU framework to work effectively, it is critical that the targeted threat intelligence process and subsequent deliverables meet the highest standards. Intelligence encompasses not only the technical details of the attack but also an understanding of the TTPs behind the attack and the attackers themselves.
During the process of producing the TTI Report, the TI provider should take into consideration a number of factors.
- TI providers must engage with the entity to obtain useful context for conducting the threat analysis. Although the entity may not always be able to share the details of sensitive incidents with the TI provider, it should still be possible to learn about the entity both through engagement with the key stakeholders and by gathering evidence of previous breaches through public sources.
- TI providers should use a broad range of sources (e.g. internet services, a mixture of public and private fora and a range of media types such as internet relay chats, email and video). The number of items in any given source type is again a useful means of measuring the likely catchment capability of any collection function. However, volume can at times undermine quality, and it is expected that the collection of sources be balanced against the ability of the TI provider to refine, analyse and discard sources in an accurate manner.
- TI providers should have a depth of sources. TI providers collecting intelligence may only use surface content from a given source, but it is also important to know that all the content of a given source can be incorporated when there is an appropriate and lawful opportunity to do so. It is therefore expected that a TI provider can provide the option to acquire data at scale and in its original context.
- TI providers should have adequate language support. Languages play an important role in providing cyber threat intelligence. Cyber threats are a global phenomenon, and a TI provider that offers little linguistic coverage of online threats will potentially miss a significant proportion of relevant information.
- TI providers should be able to use a variety of methods in intelligence gathering, for example OSINT (which is derived overtly from publicly available sources) and HUMINT (human intelligence, which is derived overtly or covertly from human sources).
- TI providers must always demonstrate strong ethical behaviour.
- TI and RT providers must work together in a collaborative, transparent and flexible manner. A TI provider must demonstrate willingness and the ability to work in this way, sharing its deliverables with its RT counterpart for review and comment. The TI provider should also demonstrate a willingness to work with the RT provider during the remainder of the TIBER-EU test. This includes the creation of testing scenarios, as well as any new intelligence requirements that occur as the red team test progresses. The TI provider is expected to provide input into the final report issued to the entity.
TIBER-EU testing phase – overview of threat intelligence and scenarios
-
For example, the national cyber security centre, national high -tech crime unit, general intelligence agency and military intelligence agency. ↩
-
It should be noted that some providers provide both TI and RT services, and entities can opt to procure such services from these providers. ↩
-
During the testing process, the RT provider may be unable to progress to the next stage owing to time constraints or because the entity has been successful in protecting itself. In such scenarios, the RT provider, with agreement from the WT and TTM, may be given a “leg-up”, where the entity essentially gives the RT provider access to its system, internal network, etc. to continue with the test and focus on the next flag/target. ↩